Darkstat v3.0.707 for Windows
컨텐츠 정보
- 5,791 조회
- 2 댓글
- 0 추천
- 목록
본문
Darkstat v3.0.707 for Windows
http://neophob.com/2007/12/darkstat-v30707-for-windows/
Darkstat Website: http://dmr.ath.cx/net/darkstat/
Darkstat for Windows port Website: http://www.neophob.com
You need WinPcap to use this tool: http://www.winpcap.org – I tested it with version 4.1 beta2.
Download:
Windows Binary
Windows Source (Ugly hack)
Example:
1 2 3 4 5 6 7 8 9 10 | c:>darkstatdarkstat 3.0.707 (built with libpcap 2.4) WinPcap devices: WARNING: if you don't see any devices here, make sure you installed WinPcap drivers http://www.winpcap.org/install/default.htm DeviceNPF_GenericDialupAdapter Description: Adapter for generic dialup and VPN capture Loopback: no DeviceNPF_{86AAB447-88AE-404D-86CB-D7E7A909B9BE} Description: Broadcom NetXtreme Gigabit Ethernet Driver Loopback: no Address Family: #2 Address Family Name: AF_INET Address: 10.226.64.65 Netmask: 255.255.255.0 Broadcast Address: 255.255.255.255.... |
As you can see in this example, 2 NIC’s are found:
1 2 | DeviceNPF_GenericDialupAdapter DeviceNPF_{86AAB447-88AE-404D-86CB-D7E7A909B9BE} |
IMPORTANT: you need to put quotation marks around your device string else you’ll receive a error like this:
1 2 3 4 5 6 | error: pcap_open_live(): Error opening adapter: The system cannot find the device specified. (20) <code> <strong>Example:</strong> c:>darkstat -i "DeviceNPF_{86AAB447-88AE-404D-86CB-D7E7A909B9BE}" or c:>darkstat -i \Device\NPF_{86AAB447-88AE-404D-86CB-D7E7A909B9BE} |
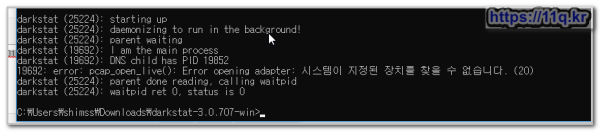
A succesfull start of darkstat look like this:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | (03516): starting up darkstat (03516): daemonizing to run in the background! darkstat (03516): parent waiting darkstat (02220): I am the main process darkstat (02220): DNS child has PID 3616 darkstat (02220): caplen is 54 darkstat (02220): capturing in promiscuous mode darkstat (02220): listening on 0.0.0.0:667 darkstat (02220): loaded 11 protos darkstat (02220): loaded 0 tcp and 0 udp servs, from total 0 darkstat (02220): chrooted into: . darkstat (02220): local_ip update(DeviceNPF_{86AAB447-88AE-404D-86CB-D7E7A909B9BE}) = 10.226.64.65 darkstat (03516): parent done reading, calling waitpid darkstat (03516): waitpid ret 0, status is 0 |
To see darkstat in action point your browser to http://127.0.0.1:667/.
Advanced:
If you want to log your darkstat stuff, you may use this example:
1 | c:>darkstat -i "DeviceNPF_{86AAB447-88AE-404D-86CB-D7E7A909B9BE}" --chroot /cygdrive/c/ --daylog daily |
To use your c: root drive you need to use /cygdrive/c/ (Cygwin syntax).
c:\Users\shimss\Downloads\darkstat-3.0.707-win>darkstat
darkstat 3.0.707 (built with libpcap 2.4)
◎ ■ ▶ ☞ ♠ 정보찾아 공유 드리며 출처는 링크 참조 바랍니다. https://11q.kr ♠
관련자료
-
링크